In this blog post, I will write about often ignored security aspects in hybrid Microsoft infrastructures (in my opinion). Because from a security perspective, I don’t see good implementations of a hybrid setup with Entra Connect Sync in most cases – mostly the setup is characterized of misconfiguration and a lack of attack surface reduction. For this reason, I will describe a handful actions you have to do to protect this neuralogic point of your hybrid setup and give you some audit and monitoring option.
I will also cover the upgrade experience and some new options with application based authentication for Entra Connect Sync, which ist release in public preview state on 28 May 2025.
But what exactly is Microsoft Entra Connect Sync?
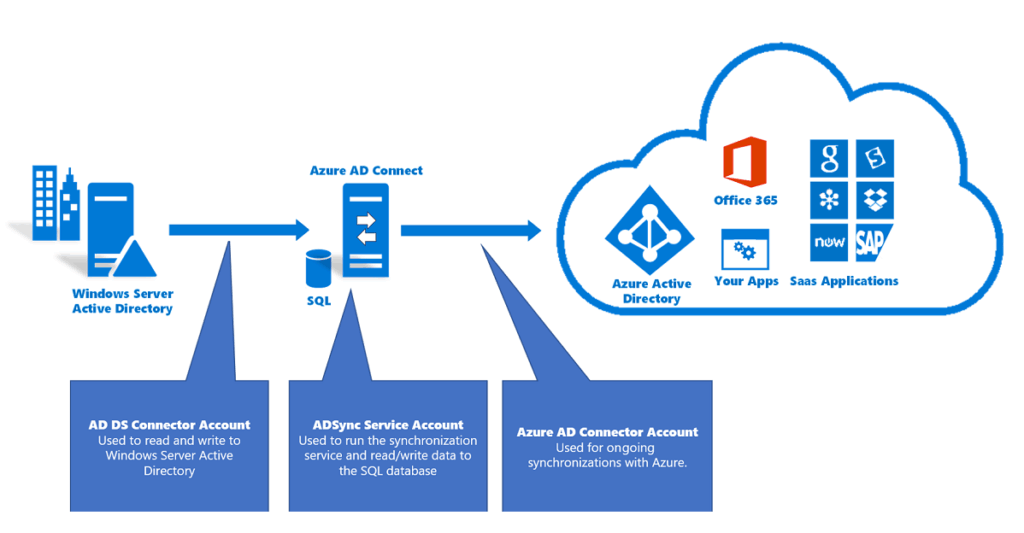
Microsoft Entra Connect Sync (formerly know as Azure AD Connect) is a on-premise managed sync service between Microsoft on-premises Active Directory (AD) and Entra ID – both also known as Identity Provider (IdP). Synchronizing identities and other objects like groups, computers and credentials and creating a realtionship of those objects between Microsoft Active Directory and Entra ID is important for a seamless user experience in a hybrid infrastructure. However, If you don’t apply security best practices for your Microsoft Entra Connect Sync Service, there are risks that both worlds can be compromised.
But first things first. Which concepts of hybrid authentications are supported by Microsoft Entra? There are three authentication methods for this:
- Identity federation with Active Directory Federation Services
- Password-hash synchronization (PHS) [default]
- Path-through authentication (PTA)
Please note, that Microsoft no longer recommends the use identity federation with Active Directory Federation Services (where possible).
Microsoft IR strongly recommends moving to native Microsoft Entra ID authentication and decommissioning AD FS (or other federated identity providers) where possible. This reduces the overall complexity of the organization’s identity plane and makes it easier to secure identities.
How does synchronization works and where are the potential attack surfaces ?
The synchronization process can typically be divided into two main parts: The synchronization of existing object information from Active Directory to Entra ID and writing back some attributes in Active Directory (for example the mS-DS-ConsistencyGUID attribute) for the synced objects.
Microsoft Entra Connect: Accounts and permissions – Microsoft Entra ID | Microsoft Learn
Hard matching synced user objects
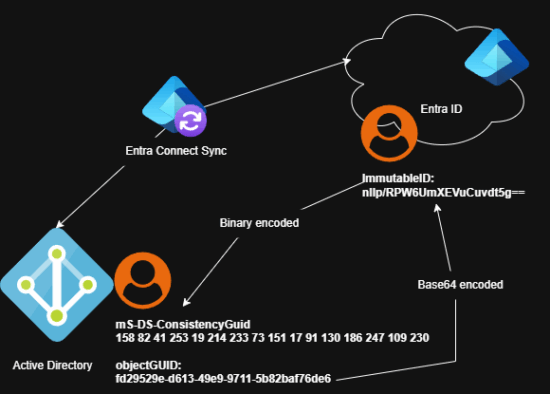
The ImmutableID is an user object attribute for each hybrid user object in Entra ID. This attribute is important because Entra Connect Sync use it to match the synced user objects with the associated user object in Active Directory. Through the ImmutableID and the mS-DS-ConsistencyGuid the synced user objects are linked, even when the object changes its name, user principal name or mail address. Even if your Entra Sync Connect service have to build from scratch, maybe because of an outage of your server, Entra Connect Sync finds the corresponding user objects and hard match them based on the ImmmutableID attribute (if the source anchor is the same). Entra Connect Sync use the mS-DS-ConsistencyGuid attribute on your Active Directory user objects as a matching key.
So, how does the hard match between the synced user objects works?
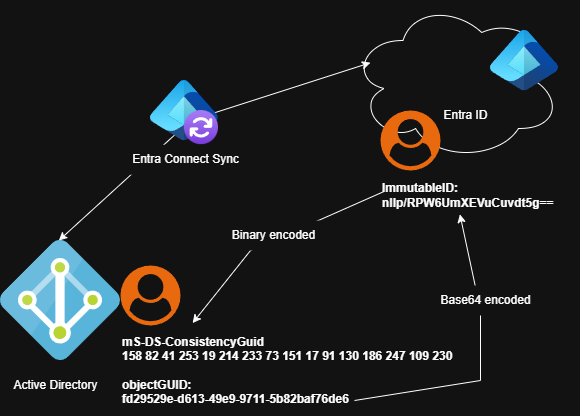
- Entra Connect Sync takes the objectGUID of a new Active Directory user object to be synchronized. (The objectGUID is unique in your forest just like the security identifier SID)
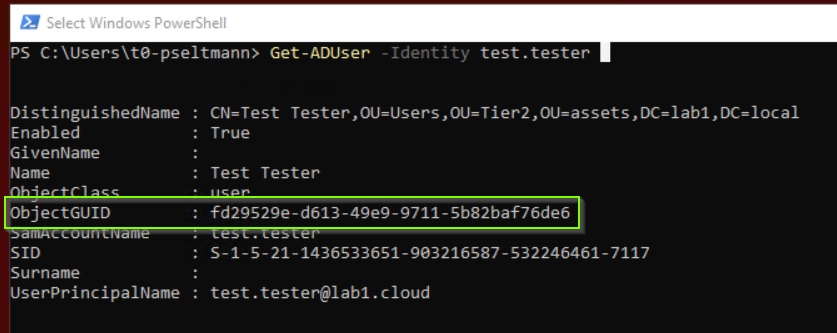
- Then Entra Connect Sync encodes the objectGUID into a Base64 value and writes it to synchronized cloud user object as ImmutableID.
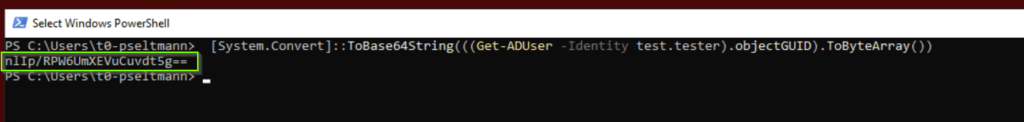
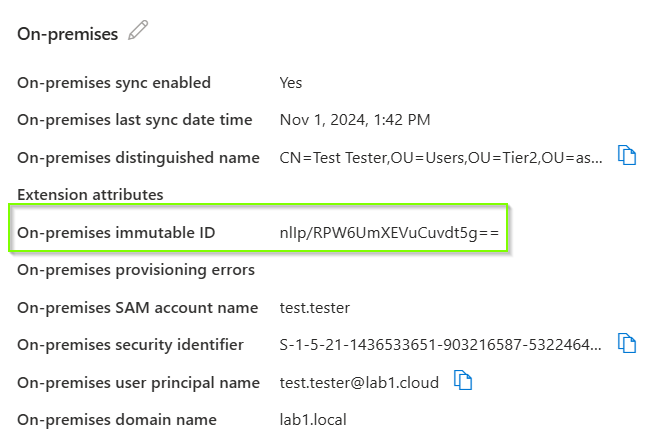
- The next sync cycle writes the ImmutableID value down to to Active Directory user object in the mS-DS-Consistency attribute. (Active Directroy sync account need write permission to this attribute, but later more…)
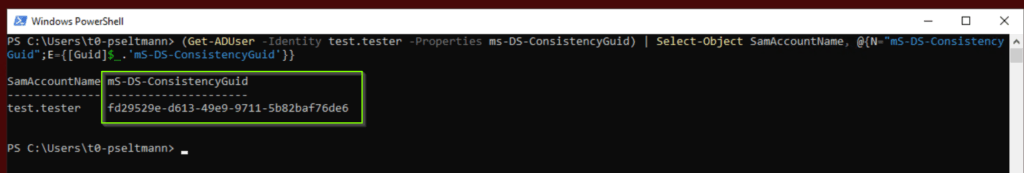
As a result, the hard match relationship between the both user accounts is established and future attribute changes (name, mail, upn, …) are synced.
Soft matching synced user objects
Soft match is used in scenarios where users have already accounts in both worlds but there isn’t already a existing relationship between the objects and the couldn’t match on the ImmutableID yet . To establish a relationship, you can match these objects based on:
- userPrincipalName or
- primary proxyAddress or
- mail attribute
For example, there is a cloud user account in Entra ID with the userPrincipalName: soft@lab1.cloud. After a while, this user needs access to local Active Directory resources and the administrator creates an Active Directory user object with the userPrincipalName: soft@lab1.cloud. If soft matching is enabled, which is in default, both user accounts are matched based on the user principal name. At this time, Active Directory becomes the source of authority for the user account and overwrites the password of the cloud user account.
Soft match is for user accounts with active assigned privileged roled disabled. But there are other potential attack path to compromise your Entra ID tenant – but later more.
Active Directory sync account
Microsoft Entra Connect: Accounts and permissions – Microsoft Entra ID | Microsoft Learn
Entra Connect uses an Active Directory sync account to process tasks in the Active Directory environments. This service account has partly high permissions which may be equivalent to a Domain Controller. The “Replication Directory Changes All” permission allows the service account to perform a DC-sync and extract and store all the Active Directory objects including the users NT password hashes on the Entra Connect Sync server self. Because of that, that the service account can “act like a Domain Controller”, the service account can access and read information about privileged users in your AD environment. Additionally, the default “MSOL_” service account get a lot of more questionable permission in a default express setup of the Entra Connect Sync Service.
All this and the facts that the Active Directory service account have to be a regular Active Directory user with a specific non-expiring password makes the Entra Connect Sync Server interesting for attacks to gain information of privileged objects in Active Directory or lateral movements to your cloud environment.
If you installed the Entra Connect Sync Service with the default express option, you can identify your Active Directors service account based on the following account prefix “MSOL_”. Each Entra Connect Sync installation uses its own Active Directory Service Account, if you selected the default express setup during installation. Hopefully you have at least two Entra Connect Sync Services installed in staging mode for disaster recovery purproses, then you have to Active Directors service accounts in your environment.
The Active Directory sync account prefixed with MSOL_ has the following permissions by default:
| permissions | notes |
| Replicate Directory Changes Replicate Directory Changes All | used to replicate objects and password hashes |
| Read/Write all properties User | write all user properties and attributes inherited down the object tree |
| Read/Write all properties iNetOrgPerson | write all iNetOrgPerson properties and attributes inherited down the object tree |
| Read/Write all properties Group | write all Group properties and attributes inherited down the object tree |
| Read/Write all properties Contact | write all Contact properties and attributes inherited down the object tree |
| Reset password | reset all user password down the object tree |
These permissions are set at the top level of your Active Directory domain and not only affect objects in the OUs you did synchronized, these permissions affect all corresponding objects in your Active Directory and is a bad approach for your whole security. Also, in previous versions of Entra Connect Sync, the default MSOL_ Active Directory sync account was assigned sensitive permissions for the AdminSDHolder template. The AdminSDHolder template is a template of permissions for your privileged Active Directory accounts.
Entra ID sync account
The Entra ID Sync account, identified by the naming prefix: sync_hostname_, is the counterpart of Active Directory sync account and is used for performing actions on synchronized objects in Entra ID. The Entra ID Sync Account has assigned a Entra ID builtin role: Directory Synchronization Accounts. This is a regular user account with a password that never expires and stored in your configuration of your Entra Connect Sync. Until august 2024, this role had sensitive permissions that were not realy required for the synchronization purpose. For example, this role had permissions to create app registrations in your tenant.
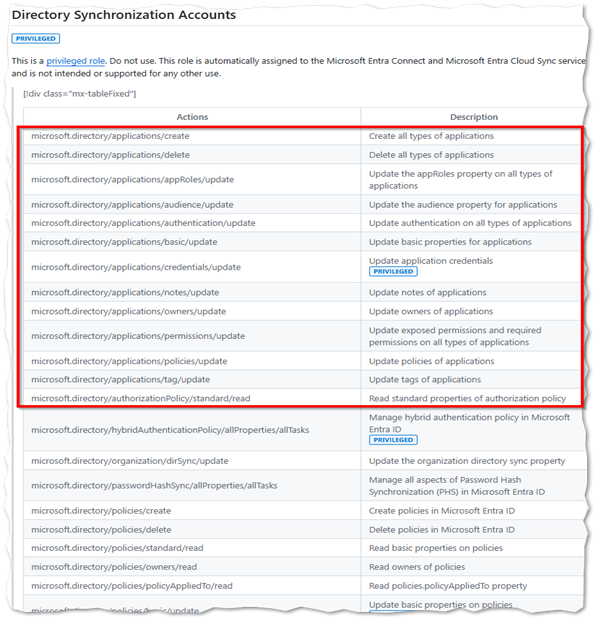
Since august 2024 the role permission have been reduced as you can check on the github commit: https://github.com/MicrosoftDocs/entra-docs/commit/6cef860add24f6741d00bda9133ec7c4be91fd81
Application based Authentication for Entra Connect Sync is now available (public preview)
As of May 28, 2025, the authentication method used by the Entra ID sync account has been changed. Instead of using a regular user object with a password that is never expires and is stored in the config of your Entra Connect Sync server, Microsoft released a new version of Entra Connect Sync which uses application bases authentication based on a service principal und certificates to reduce the attack surfaces. To benefit from this security improvement, you have to upgrade your Entra Connect Sync instances manually.
Download the latest version (2.5.3.0) from here: Download Microsoft Entra Connect from Official Microsoft Download Center
Update: My friend Jakob Frey | LinkedIn told me that the download has not been possible via the Download Center yet. You have to download the setup file from your the Microsoft Entra Connect Blade.
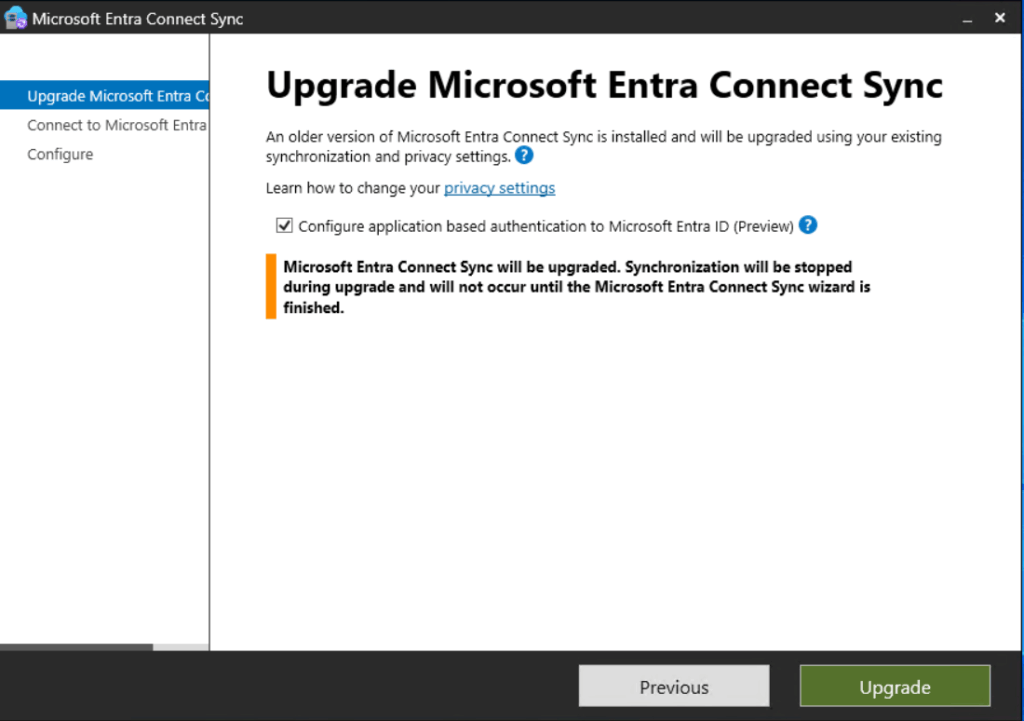
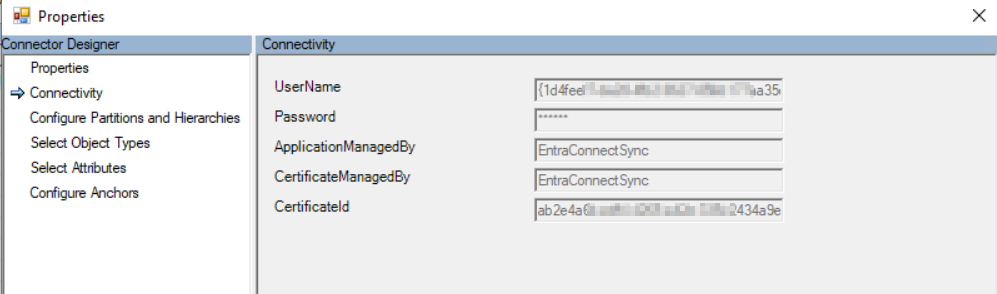
After you successfully performed the upgrade, you can see in your synchronization service manager that there is no user object used for the Entra ID Sync account. Now, there is a service principal with certificate is used for it.
You can validate this in Entra and look for a app registration like: ConnectSyncProvisioning…
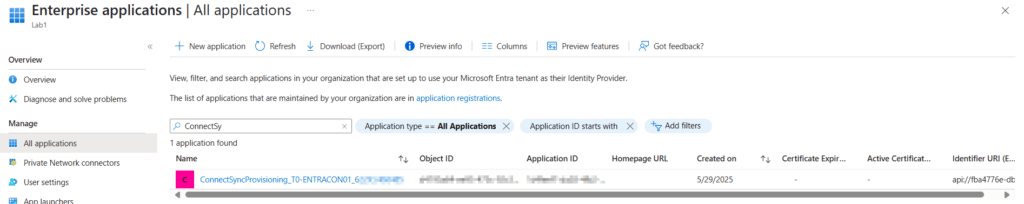
Before your applied application based authentication, you should ensure, that your Entra Connect Server has configured a TPM module to protect the private key of the certificate.
How can you reduce the attack surfaces?
As I described in the sections above, there are many Entra Connect Sync specific measures to reduce attack surfaces to think about, but there are also some fundamental approaches to improving the security of your Active Directory (hybrid).
Active Directory Sync Account
Entra Connect Sync installation method
Don’t use the express installation of Entra Connect Sync Client. Think about what are you dining. If you chose the express installation, you Active Directroy sync account get too many sensitive permissions in your tree. I also recommend installing Entra Connect Sync on a dedicated server – not on Exchange Server and Domain Controller and so on.
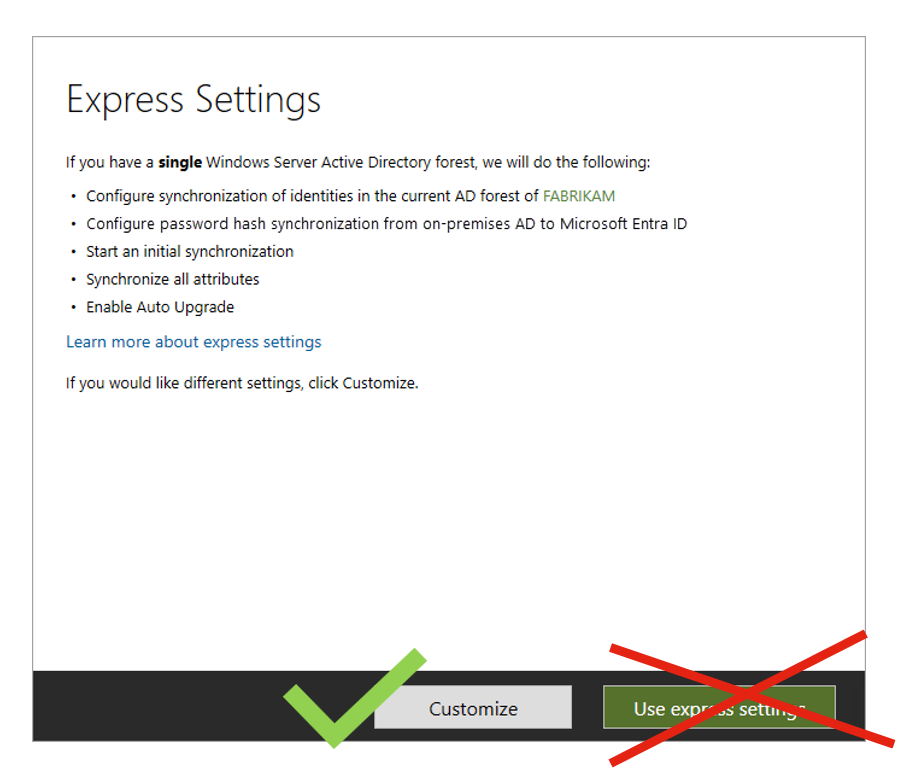
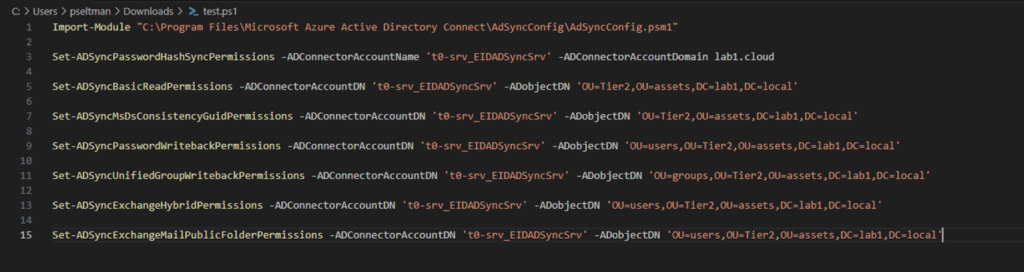
If you chose custom installation, you have to delegate permissions for your Active Directory Sync Account on the corresponding organizational units.
Active Directory tiering and hardening
The first approach, you hopefully have already implemented, is a seriously taken tiering and hardening of your Active Directory. If you had taken it seriously and living this approach, this is a effective way to make lateral movements more difficult.

Protecting Tier 0 the Modern Way | Microsoft Community Hub (Dagmar Heidecker)
Use a dedicated Active Directory Sync Account
If you have chosen the custom installation of your Entra Connect Sync client, you have to create a dedicated sync user. This user account must be a tier 0 service account.
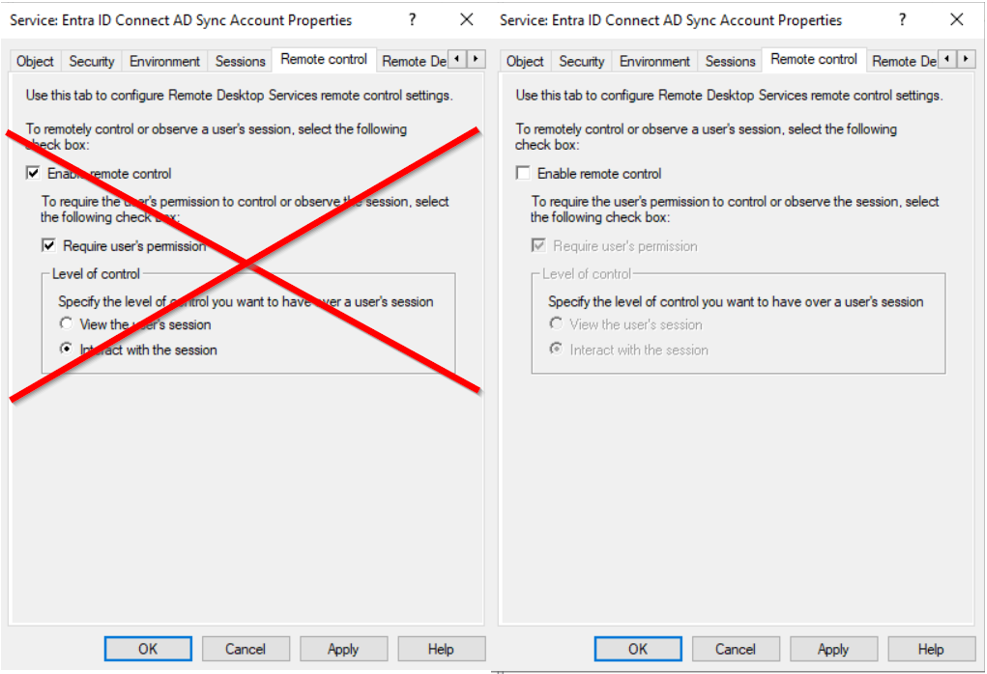
Disable unused capabilities of your Active Directory Sync Account
It is recommended to disable the following capabilities for all your regular user objects and service accounts, if you don’t need them in your environment. If you use them partially, disable these capabilities for all your service account and not just for your Active Directory Sync Account.
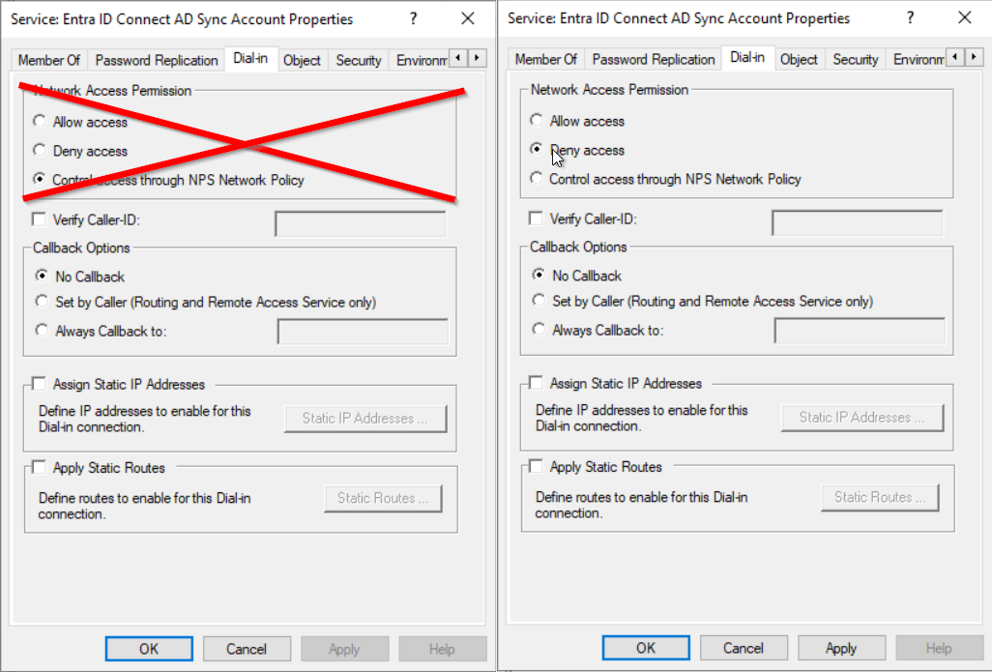
- disable remote control
- deny dial-in access
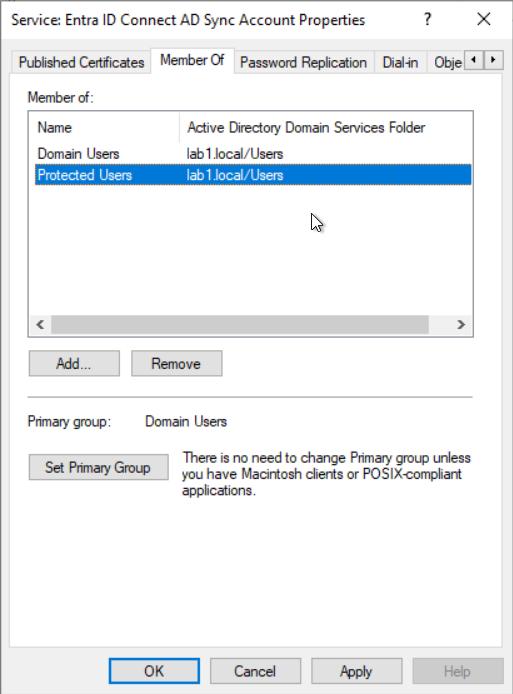
Add the Active Directory Sync Account as a member of the procted user group
As a member of the protected user group, the accounts are provided with some protection measures to prevent the use of weak authentication methods and delegation with unconstrained or constrained delegations and so on. Your find a list of all protections here: Protected Users Security Group in Windows Server | Microsoft Learn
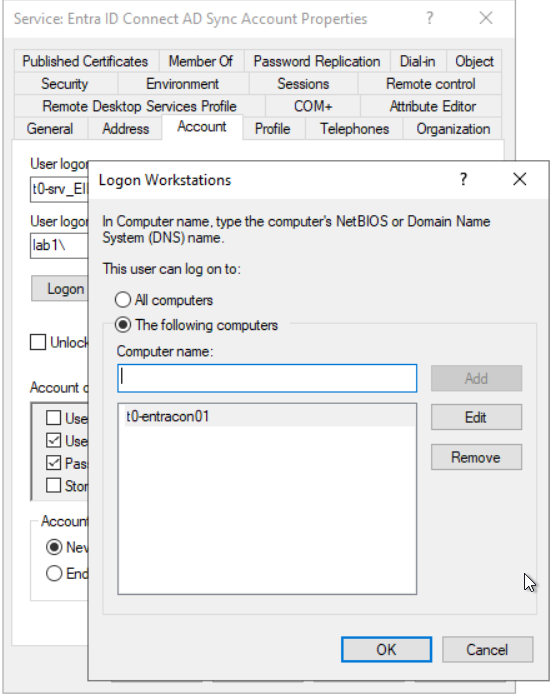
Restrict logons with authentication policy or logon workstations restrictions
If you already implemented claim based kerberos authentication, you can restrict logon and authentication parameters with authentication silo policies for Active Directory Sync Account.
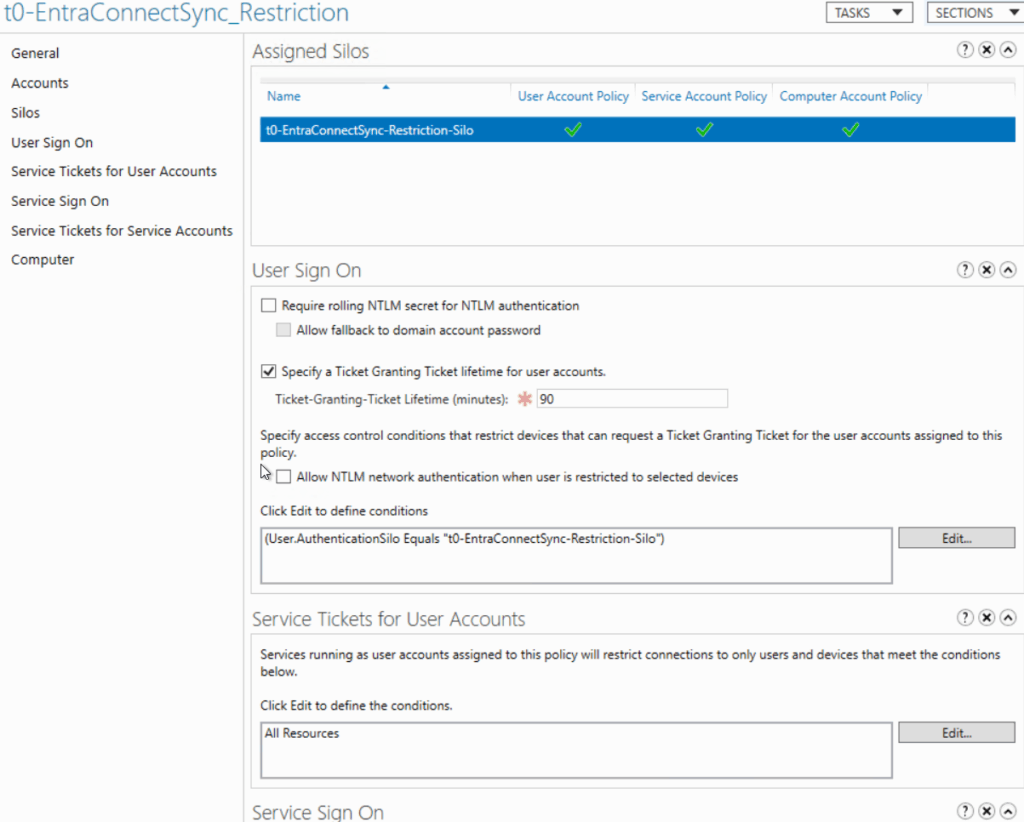
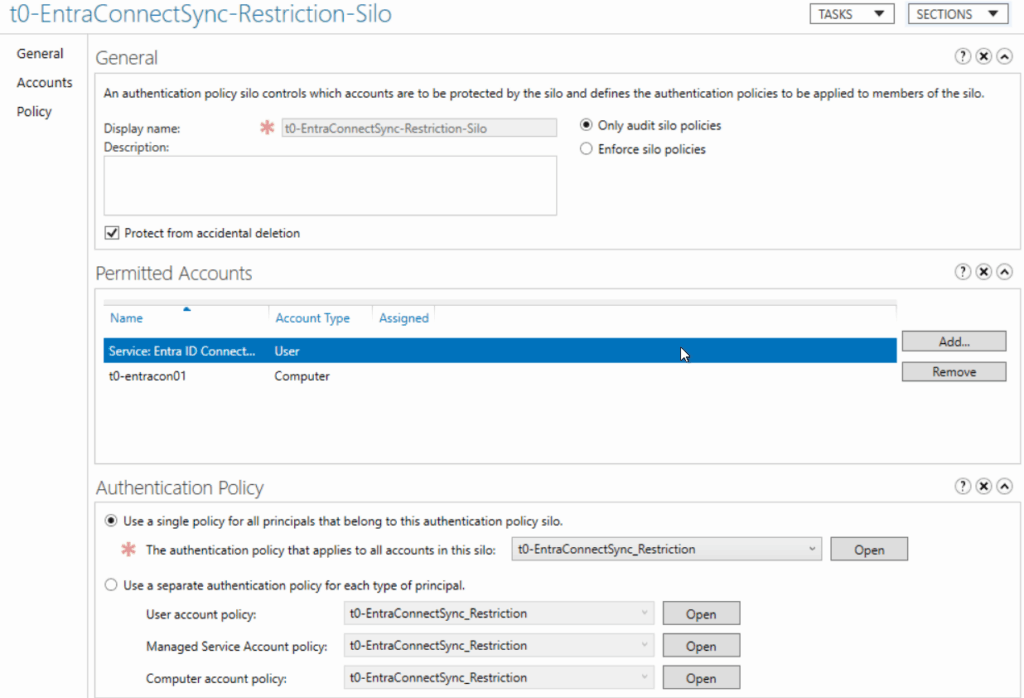
You can checked the msDS-AssignedAuthNPolicySilo & msDS-AuthNPolicySiloMembersBL attributes on the accounts that have the silo applied to confirm.
If you haven’t implement claim based kerberos authentication, you can restrict logons via workstation logon restriction in the settings of the Active Directory Sync Account themselves.
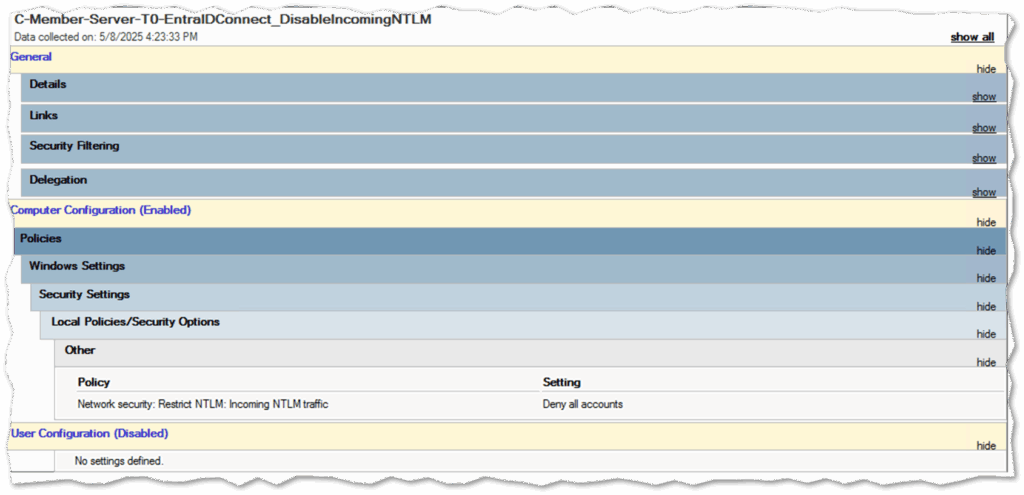
Disable incoming NTLM traffic on your Entra Connect Sync Server
To restrict the use of incoming authentication methods and force kerberos authentication, disable incoming NTLM traffic for all accounts via group policy on your Entra Connect Sync servers.
Entra ID Sync Account
Hard and Soft Matching possibilities
When you use Entra Connect, it tries to find out if a user already exists in Entra ID. It does this in two ways as I described at the beginning of this blog post:
Hard Matching: This method checks if the account in Active Directory has the same unique ID (called the “source anchor”) as the account in Entra ID (called “ImmutableID”).
Soft Matching: This method looks at the user’s userPrincipalName, proxyAddress or email attribute. If some one match, it assumes it’s the same user.
These matching methods can help during migrations. But be careful – they also open up security risks. For example, someone could take over an account if these settings are not properly managed. Because of that, it is the best to turn off these options during normal operation of Entra Connect Sync.
If you want to check whether hard or soft matching is enabled, you can use these Microsoft Graph commands:
Connect-MgGraph -TenantId "<DEIN_TENANT_ID>" -Scopes "OnPremDirectorySynchronization.ReadWrite.All" -NoWelcome
try {
$syncConfig = Get-MgDirectoryOnPremiseSynchronization
if ($syncConfig -and $syncConfig.Features) {
$syncConfig.Features | Format-List
} else {
exit
}
}
catch {
Write-Error "$_"
}
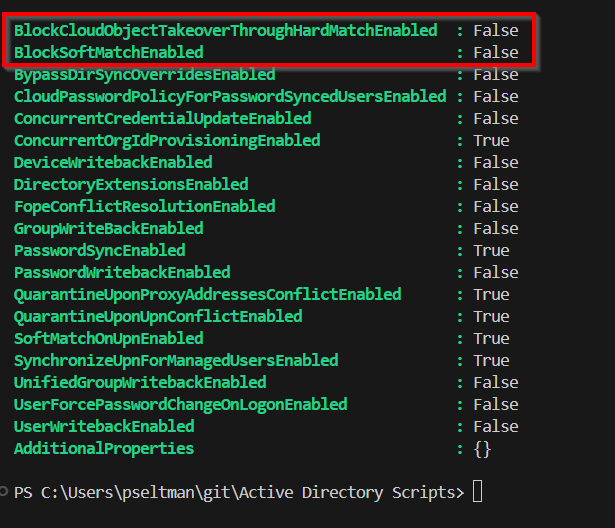
To disable hard and soft match capabilities, run the following commands:
Connect-MgGraph -TenantId "<DEIN_TENANT_ID>" -Scopes "OnPremDirectorySynchronization.ReadWrite.All" -NoWelcome
try {
$sync = Get-MgDirectoryOnPremiseSynchronization
if (-not $sync) {
throw "Could not retrieve on-premises directory synchronization configuration."
}
$config = @{
Features = @{
BlockCloudObjectTakeoverThroughHardMatchEnabled = $true
BlockSoftMatchEnabled = $true
}
}
Update-MgDirectoryOnPremiseSynchronization -OnPremisesDirectorySynchronizationId $sync.Id -BodyParameter $config
Write-Host "Hard and soft match synchronization settings updated successfully." -ForegroundColor Green
}
catch {
Write-Error "Failed to update synchronization settings: $_"
}
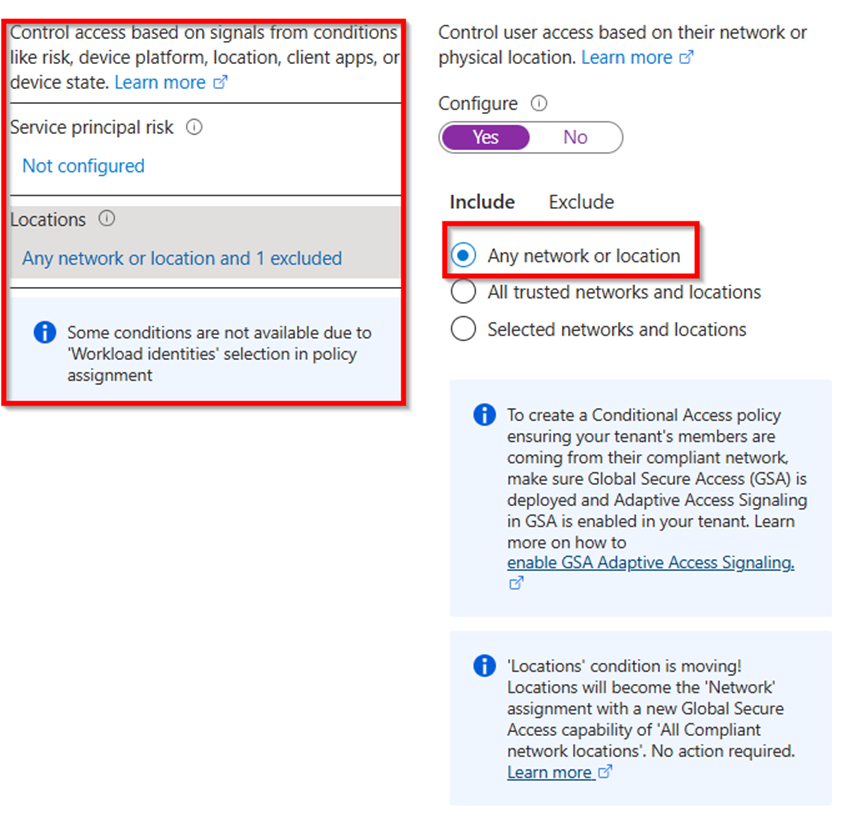
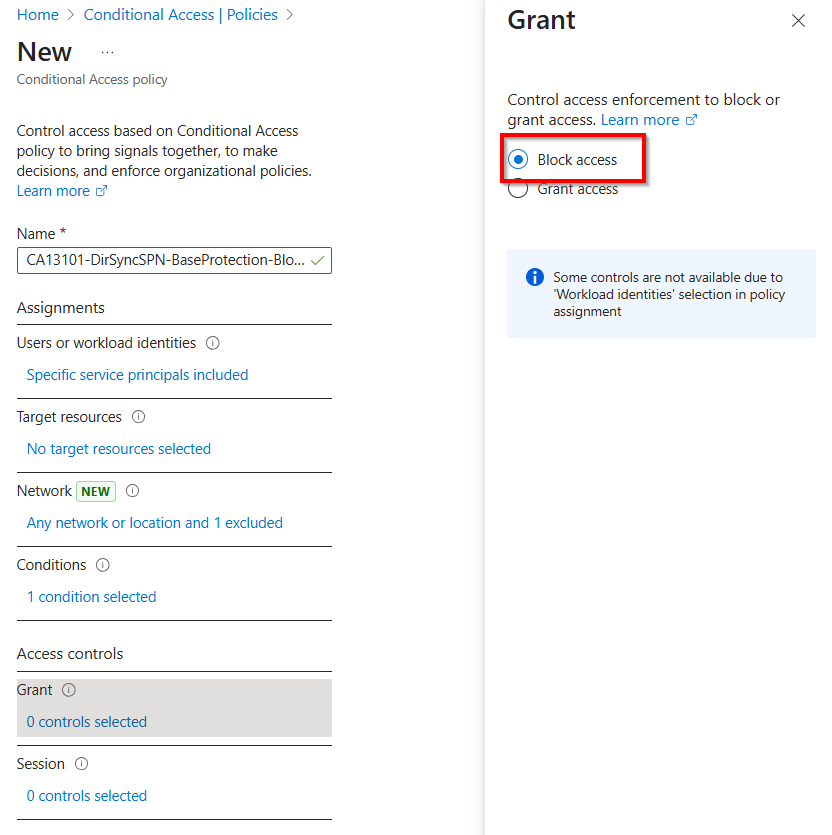
Restrict access via Conditional Access Policies
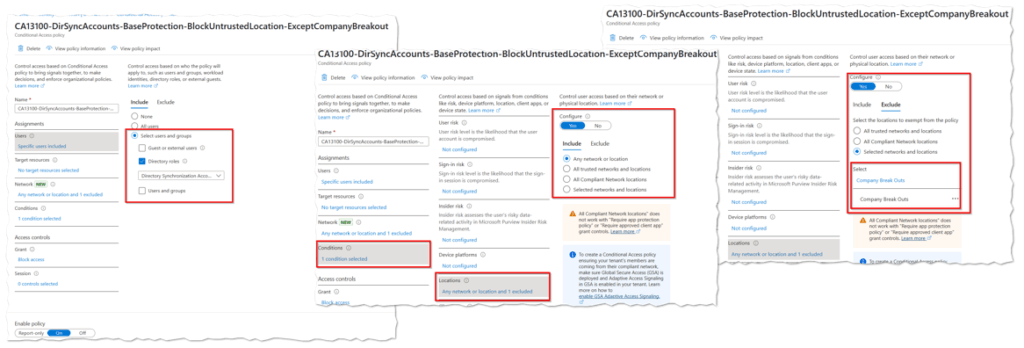
Entra Connect Sync until version 2.5.3.0 or without application based authentication applied
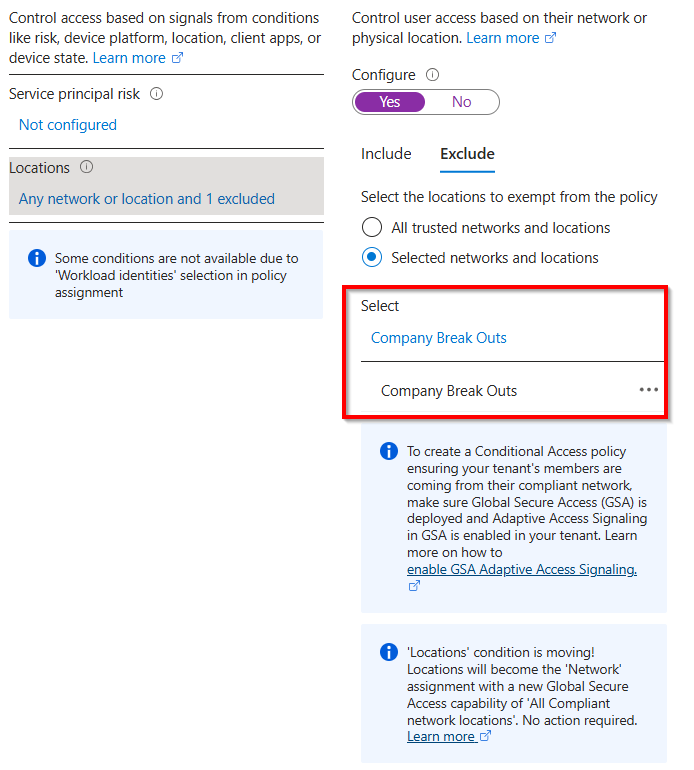
If you use a Entra Connect Sync version older then 2.5.3.0, you should restrict the use of your the Entra Connect Sync Account user object sync_hostname_ to your public ip address (company breakout).
Entra Connect Sync version 2.5.3.0 and newer with application based authentication enabled
If you use a Entra Connect Sync version 2.5.3.0 and newer and already applied the authentication based authentication, your Entra Connect Sync client use a service principal instead of a regular user object for synchronization.
You should restrict the use of your the Entra Connect Sync Service Principal to your public ip address (company breakout). To protect a service principal with a conditional access policy, you must own licesenses for Workload Identity Protection!
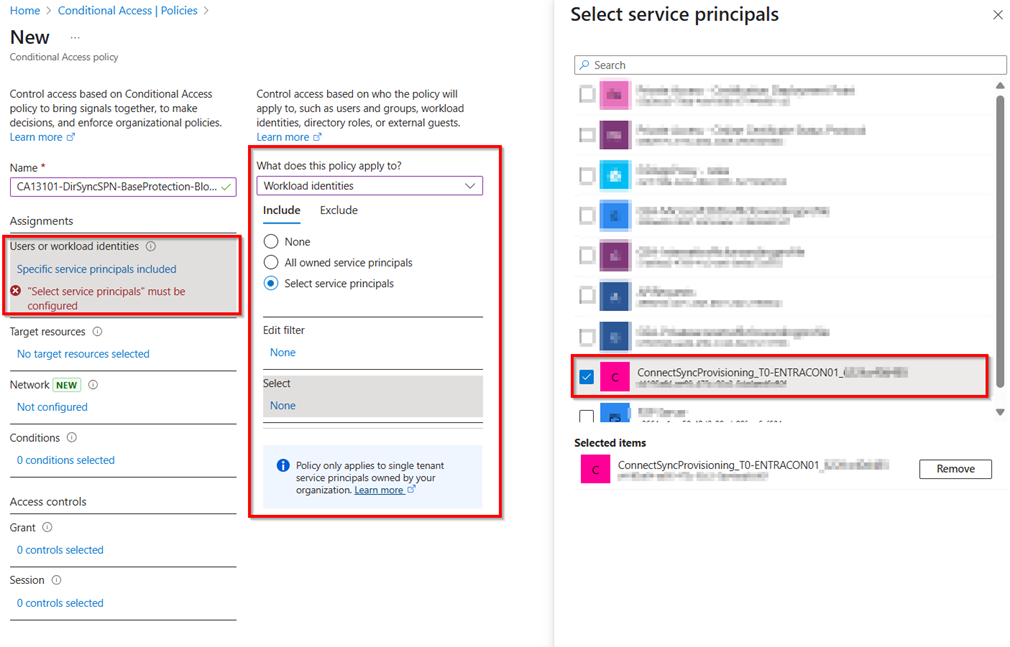
Monitor changes
You should monitor changes to the Entra Connect Sync account or service principal and monitor what actions they perform. If you use Entra Connect Sync unti version 2.5.3.0, you can use the following KQL to query audit logs and track activities on chages targeting the Entra Connect Sync Account:
let eidcAccounts = dynamic([
'Your Sync Account SPN'
]);
let excludes = dynamic([
'Microsoft Approval Management',
'Microsoft Azure AD Group-Based Licensing',
'Microsoft Substrate Management'
]);
AuditLogs
| where TimeGenerated > ago(30d)
| where isnotempty(TargetResources)
| mv-expand TargetResources
| where TargetResources.userPrincipalName in~ (eidcAccounts)
| extend Initiator = tostring(InitiatedBy.user.userPrincipalName)
| where Initiator !in~ (excludes)
| project
TimeGenerated,
TargetUPN = TargetResources.userPrincipalName,
OperationName,
Initiator
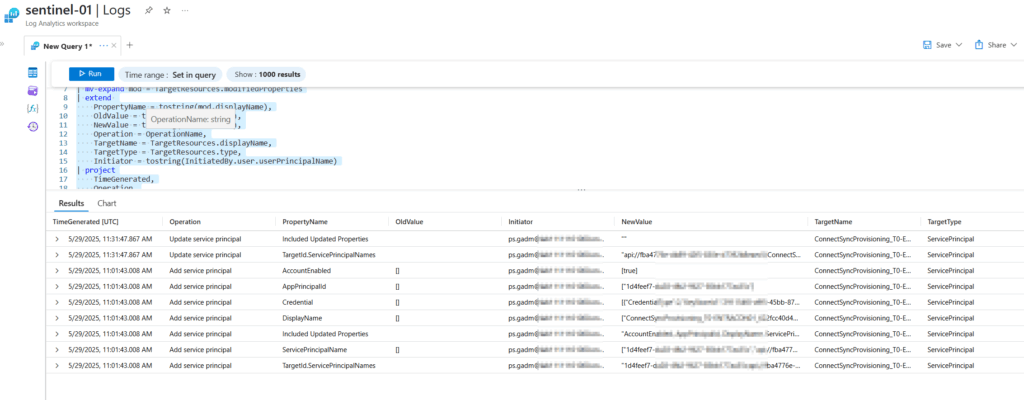
If you already updated to version 2.5.3.0 or newer, your have to audit changes on the service principal. You can use the following KQL to monitor modification in the service principal:
let targetObjectId = 'SPN ObjectID';
AuditLogs
| where TimeGenerated > ago(30d)
| where isnotempty(TargetResources)
| mv-expand TargetResources
| where TargetResources.id == targetObjectId
| mv-expand mod = TargetResources.modifiedProperties
| extend
PropertyName = tostring(mod.displayName),
OldValue = tostring(mod.oldValue),
NewValue = tostring(mod.newValue),
Operation = OperationName,
TargetName = TargetResources.displayName,
TargetType = TargetResources.type,
Initiator = tostring(InitiatedBy.user.userPrincipalName)
| project
TimeGenerated,
Operation,
PropertyName,
OldValue,
NewValue,
Initiator,
TargetName,
TargetType
| sort by TimeGenerated desc
Disabling Seamless SSO in Entra Connect Sync improve your security
Microsoft Entra Connect Sync seamless Single Sign-On (SSO) makes it easier for users to access apps connected to Microsoft Entra ID and automatically signing users in when they are accessing them from an Active Directory joined device.
But can also be a risk. Daniel Bradley has explained in his insightful blogpost potential risks and how you can mitigate them.

But be aware, If you use terminal servers or vdi-systems without at least a hybrid-join, you interrupted the single sing-on experience for your users on these systems.