Should you exclude “Microsoft Intune Enrollment” from your compliance CAP or not?
Hello everyone, in this post, we will discuss a conditional access configuration I have seen in many Entra…
Mastering App Control for Business | Part 7: Maintaining your policies with Azure DevOps (or PowerShell)
Hello everyone, in this last post in this series, I will describe how you can maintain your App…
Mastering App Control for Business | Part 6: Sign, apply and remove signed policies
HI folks, in this post, I continue my blog series about Application Control for Business and take a…
Mastering App Control for Business | Part 5: Create a base policy for fully managed devices
Hi folks, in this blog post, I will continue my series on Application Control for Business and explain…
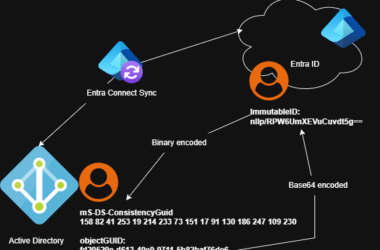
Entra Connect Sync – Attack Surface Reductions
In this blog post, I will write about often ignored security aspects in hybrid Microsoft infrastructures (in my…
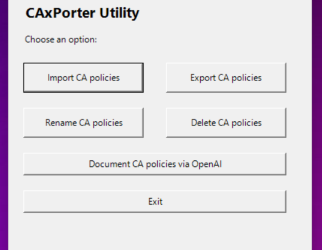
CAxPorter Utility helps to manage Conditional Access Policies
Broadly spreaded over the last two and a half years, I developed some PowerShell Script for managing bulk…
Mastering App Control for Business | Part 4: How to create a “starter base policy” for lightly managed devices
In the last three blog posts about App Control for Business, I talked a lot of theory and…
Session token lifetime: require reauthentication every time
Every time I talk about Conditional Access I say: “You must think about it as an identity firewall…
Mastering App Control for Business | Part 3: Application ID Tagging Policies & managed Installer
Hello everyone. In my last blog post Mastering App Control for Business | Part 2: Policy Templates &…
Mastering App Control for Business | Part 2: Policy Templates & Rule Options
In my last blog post Mastering App Control for Business | Part 1: Introduction & Key Concept I…