Every time I talk about Conditional Access I say: “You must think about it as an identity firewall – whitelist your needed identity access scenarios and block all others”. Why that, I prefer the persona-based Conditional Access Framework from the Azure Architect Center. The Framework supports you by implementing your identity-based firewall.
I already wrote a blog post (in german) about this framework and how you can adopt it: Persona-basiertes Conditional Access Framework für sicheren Zugriff durch die “Identitätsfirewall”.
In some cases the customer wished there was a possibility to enforce a full re-authentication instead of using a device bounded cashed refresh token. With the March 2025 updates of Microsoft Entra, Microsoft has introduced the general availability of such possibility. Now, you can configure session lifetime to enforce a re-authentication every time.
What’s New Microsoft Entra releases and announcements – Microsoft Entra | Microsoft Learn
Before we talk about this new possibility to handle the token lifetimes, I will give you an quick overview what Primary Refresh Tokens (PRTs) are.
What is a Primary Refresh Token?
Primary Refresh Tokens (PRTs) are tokens generated on a successful authentication in Microsoft Entra ID and contains multi-factor claims. They are a key part of the authentication process and help enable smoother access to Microsoft 365 services and apps.
Primary Refresh Tokens are automatically renewed when the conditions like device compliance, user activity are true. This means, you don’t need to re-authenticate with MFA on a device were the primary refresh token can be renewed automatically. By default, the inactive token time before a MFA re-authentication on the same device is required is 90 days. This default behavior van be changed using session lifetime policies.
More details: Understanding Primary Refresh Token (PRT) in Microsoft Entra ID – Microsoft Entra ID | Microsoft Learn
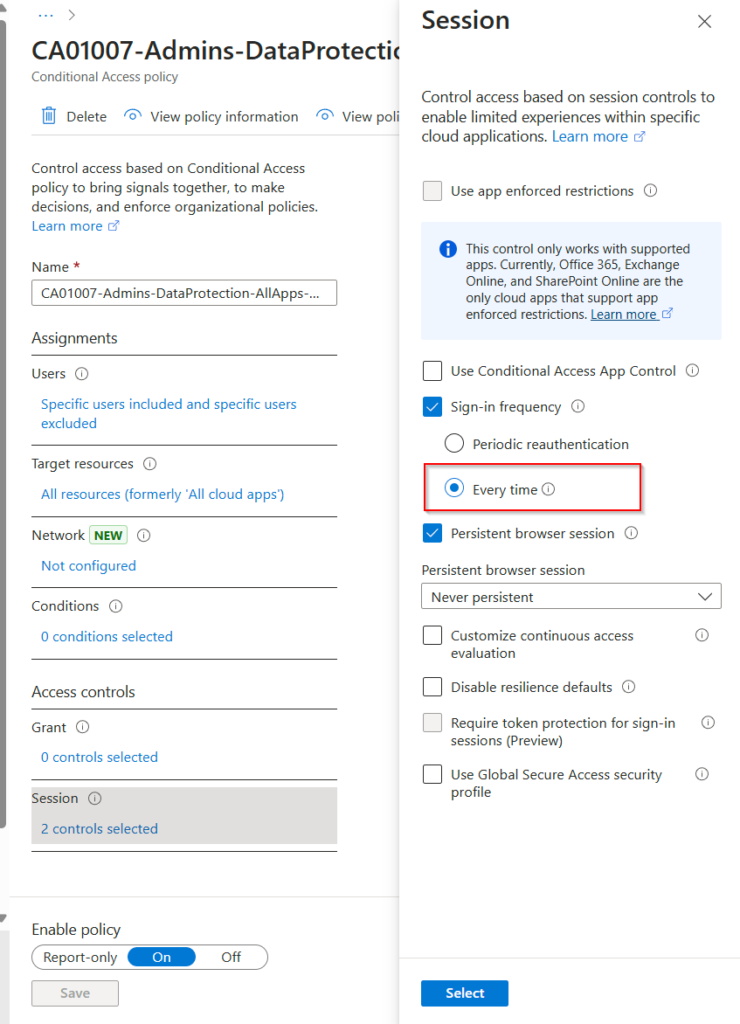
Require reauthentication every time
The default behavior I was explained in the section above can be significant modified with session token lifetime policies. As I wrote in the post introduction, there are some cases where a full re-authentication can be usefull. Now you do this with the new session policy: Require reauthentication every time
My first thought was: Jep now, we can strengthen the security for privileged users by enforcing a real re-authentication every time a they access a cloud-based privileged access workstations (PAW) for secure remote administration. But there are also other possibilities:
- Accessing sensitive applications.
- Securing resources behind VPN or Network as a Service (NaaS) providers.
- Securing privileged role elevation in PIM.
- Protecting user sign-ins.
- Protecting risky users and risky sign-ins identified by Microsoft Entra ID Protection.
- Securing sensitive user actions like Microsoft Intune enrollment.
Conditional Access adaptive session lifetime policies – Microsoft Entra ID | Microsoft Learn
How is the end-user experience of this new session lifetime policy? If your identity is in scope of a “require reauthentication every time” policy and you need to logon to different admin portals, such as Intune admin portal and Entra admin portal in the same browser but in different tabs, you must authenticate twice.
But keep in mind that triggering re-authentication to frequently, also when this session policies points to admin personas in my opinion, it can cause frustration.